Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right. Select and Place:
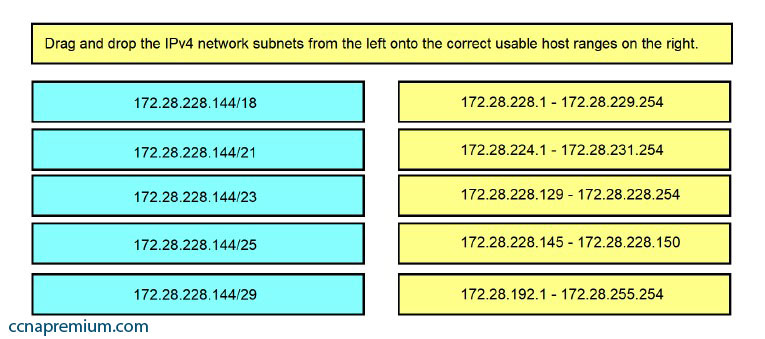
Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right. Select and Place:

Refer to the exhibit. Drag and drop the networking parameters from the left on to the correct values on the right.
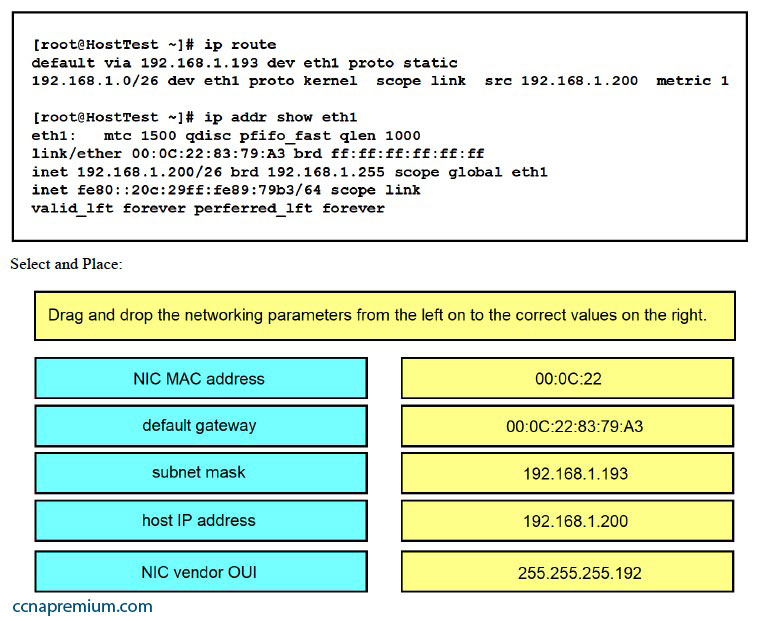
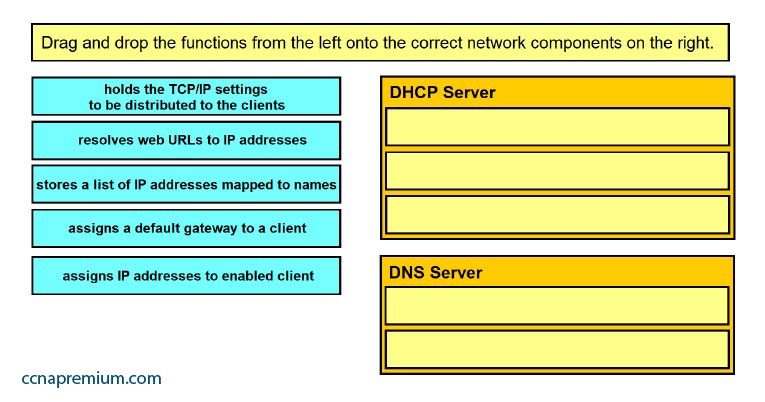
Select and Place:
You are a network administrator for your organization. Your organization has two Virtual LANs (VLANs) named Marketing and Production. All switches in the network have both VLANs configured on them. Switches A, C, F, and G have user machines connected for both VLANs, while switches B, D, and E have user machines connected for the Production VLAN only.
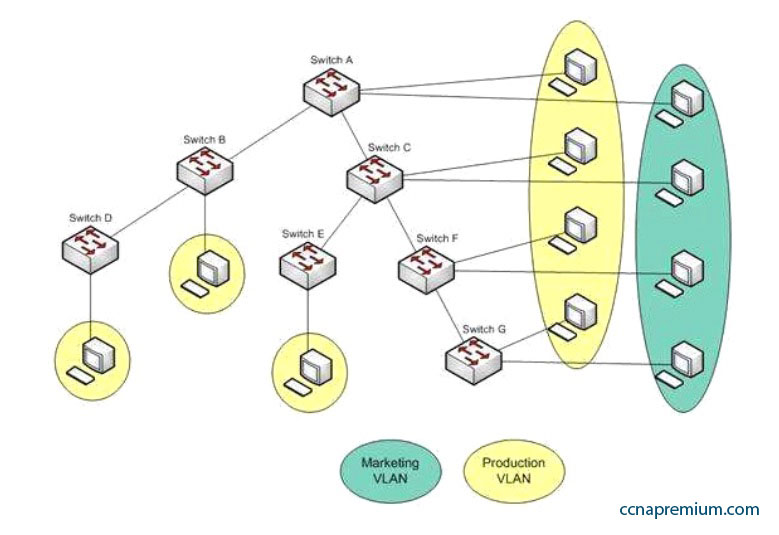
To reduce broadcast traffic on the network, you want to ensure that broadcasts from the Marketing VLAN are flooded only to those switches that have Marketing VLAN users. Which Cisco switch feature should you use to achieve the objective?
A. PVST
B. RSTP
C. VTP Pruning
D. Dynamic VLANs
The workstation at 10.0.1.3 sends a packet to the workstation at 10.1.1.3.
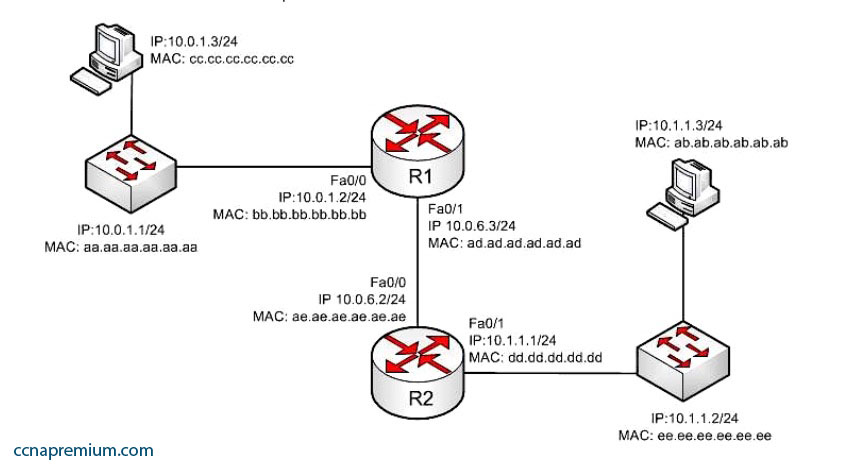
When the packet leaves the R2 router, what addresses will be located in the header? (Choose two.)
A. Source MAC bb.bb.bb.bb.bb.bb Dest MAC ab.ab.ab.ab.ab.ab
B. Source MAC dd.dd.dd.dd.dd.dd Dest MAC ab.ab.ab.ab.ab.ab
C. Source MAC ee.ee.ee.ee.ee.ee Dest MAC ab.ab.ab.ab.ab.ab
D. Source IP 10.0.1.3 Dest IP 10.1.1.3
E. Source IP 10.0.1.1 Dest IP 10.1.1.2
F. Source IP 10.0.1.2 Dest IP 10.1.1.3
G. Source IP 10.0.1.1 Dest IP 10.1.1.3
How many collision and broadcast domains are in the network shown below?
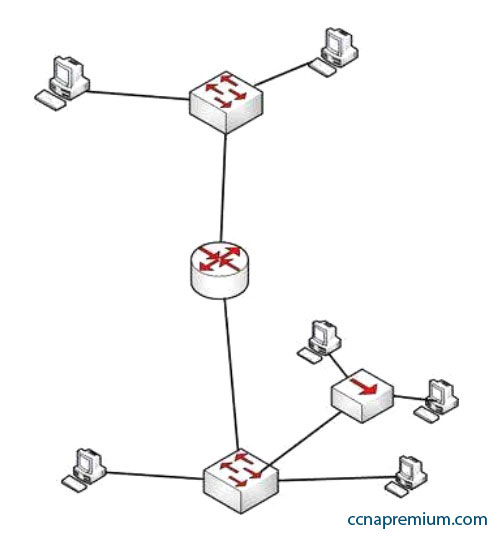
A. 4 collision domains and 3 broadcast domains
B. 7 collision domains and 2 broadcast domains
C. 8 collision domains and 1 broadcast domain
D. 6 collision domains and 2 broadcast domains
Your network is configured as shown in the following exhibit. When you trace traffic sourced from R3 destined for a LAN network off of R2 (not shown in the diagram), you see the traffic is being forwarded from R1 to ISP1 rather than to R2.
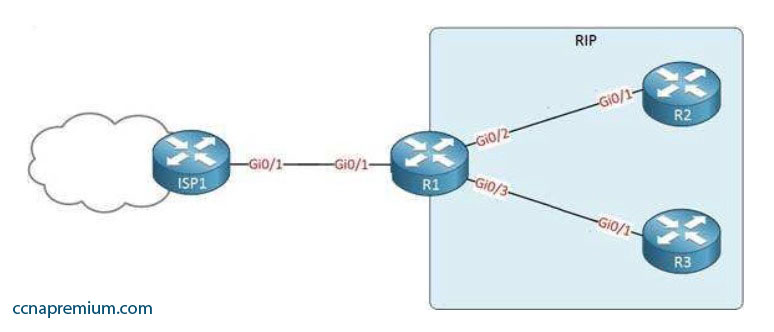
Which of the following issues could NOT be causing this behavior?
A. The network command has not been executed on the interface leading to the LAN off R2
B. A default route exists on R1 that leads to ISP1
C. RIPv2 has not been enabled on R2
D. The passive interface command has been issued on the Gi0/4 interface of R1
Examine the following diagram:
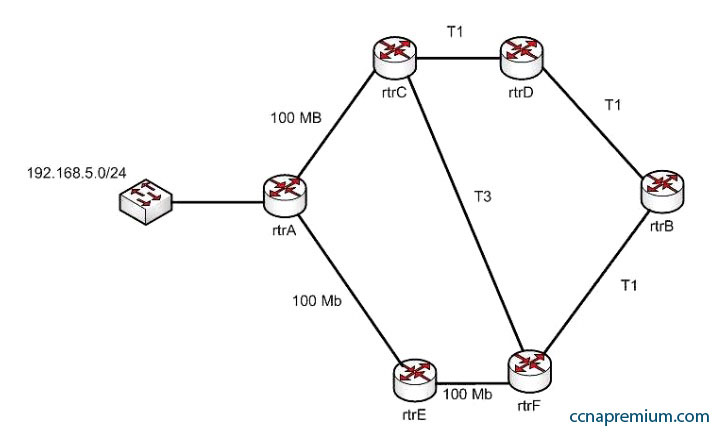
While troubleshooting an OSPF routing problem, you need to determine the cost for Router F to reach the 192.168.5.0 24 network via the best route. What will that cost be?
A. 2
B. 3
C. 7
D. 110
Host A is configured for DHCP, but it is not receiving an IP address when it powers up. What is the most likely cause?
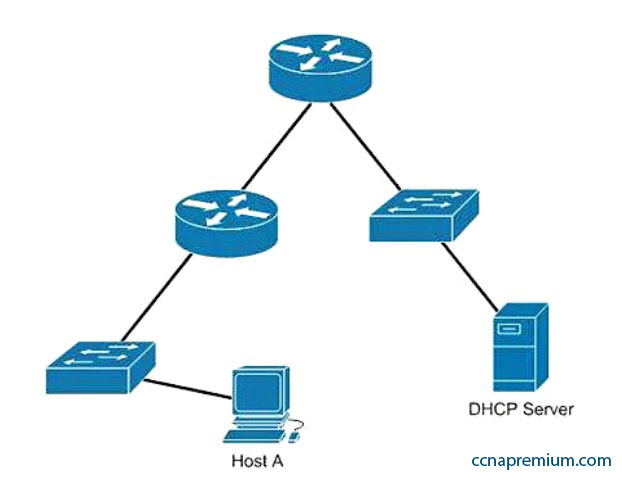
A. The DHCP server is on the wrong subnet.
B. Routers do not forward broadcast traffic.
C. The DHCP server is misconfigured.
D. Port security is enabled on the switch.
Your company’s network must make the most efficient use of the IP address space. In the following diagram, the circles define separate network segments. The requirements of each network segment are given in the diagram.

Users complain of connectivity issues. You need to discover the problems with the network configuration. What are the three problems with the network diagram? (Choose three.)
A. The 172.16.1.0/30 segment requires more user address space.
B. The 172.16.2.0/26 segment requires more user address space.
C. The 172.16.3.0/25 segment requires more user address space.
D. The 172.16.2.64/26 segment requires more user address space.
E. Interface fa0/2 has an IP address that belongs to the 172.16.2.64/26 segment.
F. Interface fa0/4 has an IP address that belongs to the 172.16.2.0/26 segment.
G. Interface fa0/3 has an IP address outside the 172.16.3.0/25 segment.