When you are troubleshooting an ACL issue on a router, which command would you use to verify which interfaces are affected by the ACL?
A. show ip access-lists
B. show access-lists
C. show interface
D. show ip interface
E. list ip interface
When you are troubleshooting an ACL issue on a router, which command would you use to verify which interfaces are affected by the ACL?
A. show ip access-lists
B. show access-lists
C. show interface
D. show ip interface
E. list ip interface
Refer to exhibit.
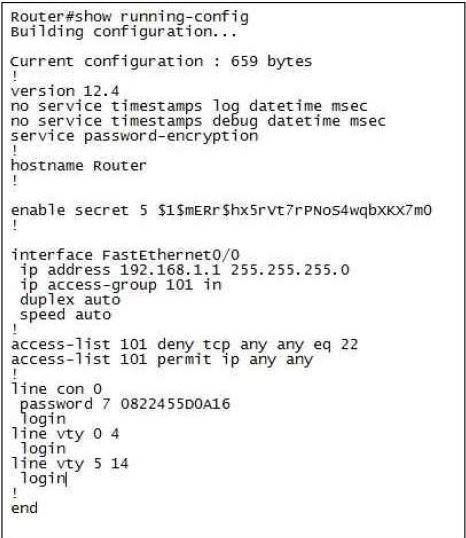
A network administrator cannot establish a Telnet session with the indicated router. What is the cause of this failure?
A. A Level 5 password is not set.
B. An ACL is blocking Telnet access.
C. The vty password is missing.
D. The console password is missing.
Which statement about access lists that are applied to an interface is true?
A. You can place as many access lists as you want on any interface.
B. You can apply only one access list on any interface.
C. You can configure one access list, per direction, per Layer 3 protocol.
D. You can apply multiple access lists with the same protocol or in different directions.
Which item represents the standard IP ACL?
A. access-list 110 permit ip any any
B. access-list 50 deny 192.168.1.1 0.0.0.255
C. access list 101 deny tcp any host 192.168.1.1
D. access-list 2500 deny tcp any host 192.168.1.1 eq 22
A network administrator is configuring ACLs on a Cisco router, to allow traffic from hosts on networks 192.168.146.0, 192.168.147.0, 192.168.148.0, and 192.168.149.0 only.
Which two ACL statements, when combined, would you use to accomplish this task? (Choose two.)
A. access-list 10 permit ip 192.168.146.0 0.0.1.255
B. access-list 10 permit ip 192.168.147.0 0.0.255.255
C. access-list 10 permit ip 192.168.148.0 0.0.1.255
D. access-list 10 permit ip 192.168.149.0 0.0.255.255
E. access-list 10 permit ip 192.168.146.0 0.0.0.255
F. access-list 10 permit ip 192.168.146.0 255.255.255.0
What can be done to secure the virtual terminal interfaces on a router? (Choose two.)
A. Administratively shut down the interface.
B. Physically secure the interface.
C. Create an access list and apply it to the virtual terminal interfaces with the access-group command.
D. Configure a virtual terminal password and login process.
E. Enter an access list and apply it to the virtual terminal interfaces using the access-class command.
Which two commands correctly verify whether port security has been configured on port FastEthernet 0/12 on a switch? (Choose two.)
A. SW1#show port-secure interface FastEthernet 0/12
B. SW1#show switchport port-secure interface FastEthernet 0/12
C. SW1#show running-config
D. SW1#show port-security interface FastEthernet 0/12
E. SW1#show switchport port-security interface FastEthernet 0/12
Refer to the exhibit.
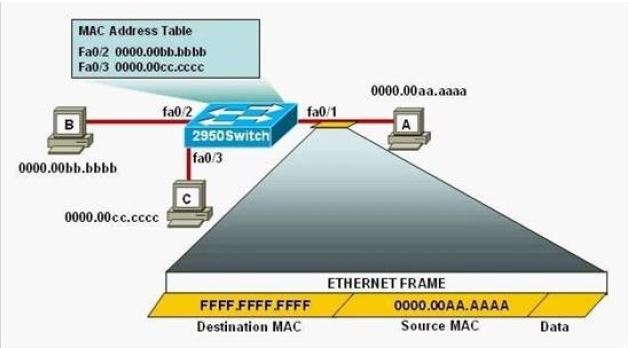
The following commands are executed on interface fa0/1 of 2950Switch.
2950Switch(config-if)# switchport port-security
2950Switch(config-if)# switchport port-security mac-address sticky
2950Switch(config-if)# switchport port-security maximum 1
The Ethernet frame that is shown arrives on interface fa0/1. What two functions will occur when this frame is received by 2950Switch? (Choose two.)
A. The MAC address table will now have an additional entry of fa0/1 FFFF.FFFF.FFFF.
B. Only host A will be allowed to transmit frames on fa0/1.
C. This frame will be discarded when it is received by 2950Switch.
D. All frames arriving on 2950Switch with a destination of 0000.00aa.aaaa will be forwarded out fa0/1.
E. Hosts B and C may forward frames out fa0/1 but frames arriving from other switches will not be forwarded out fa0/1.
F. Only frames from source 0000.00bb.bbbb, the first learned MAC address of 2950Switch, will be forwarded out fa0/1.
What two things will a router do when running a distance vector routing protocol? (Choose two.)
A. Send periodic updates regardless of topology changes.
B. Send entire routing table to all routers in the routing domain.
C. Use the shortest-path algorithm to the determine best path.
D. Update the routing table based on updates from their neighbors.
E. Maintain the topology of the entire network in its database.
Which command is used to display the collection of OSPF link states?
A. show ip ospf link-state
B. show ip ospf lsa database
C. show ip ospf neighbors
D. show ip ospf database